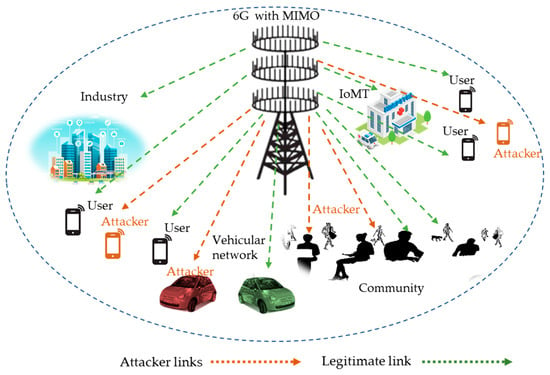
Have you ever wondered how to establish secure and stealthy communication networks?
When it comes to communication networks, security is essential for protecting sensitive information. By establishing secure and stealthy communication networks, you can ensure that your data is protected from unauthorized access. In this article, we will discuss how you can create secure and stealthy communication networks to safeguard your information.
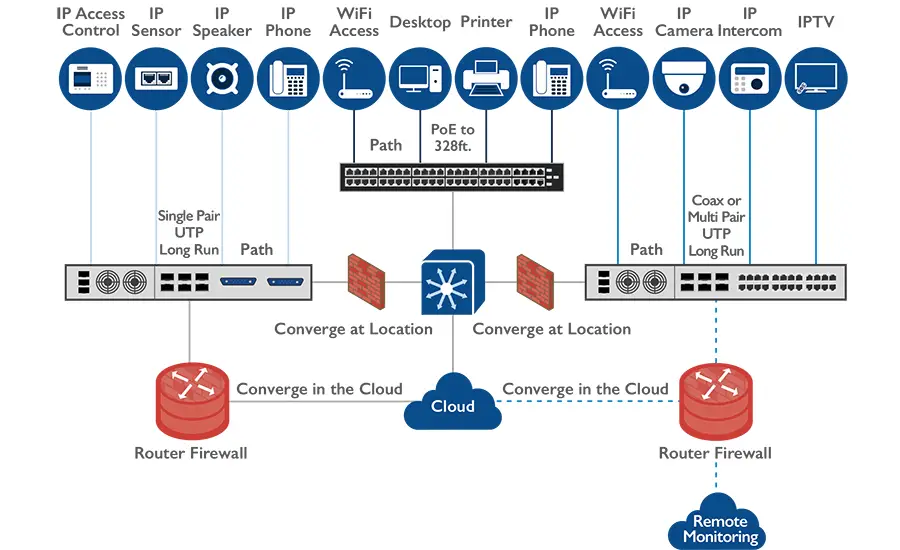
Understanding secure communication networks
Secure communication networks use encryption protocols to protect data as it is transmitted over the network. This prevents unauthorized access and ensures that only the intended recipient can access the information. By using secure communication networks, you can prevent cyber attacks and data breaches that could compromise your sensitive information.
How encryption works in secure communication networks
Encryption is the process of converting data into a coded form that can only be decrypted by authorized parties. This ensures that even if the data is intercepted, it cannot be read without the decryption key. Encryption algorithms are used to scramble the data, making it unreadable to anyone without the key. This provides a secure way to transmit sensitive information over the network.
The importance of secure communication networks
Secure communication networks are essential for protecting sensitive information from unauthorized access. By encrypting data as it is transmitted over the network, you can prevent hackers and cybercriminals from intercepting and reading the information. This ensures that your data remains confidential and secure, reducing the risk of data breaches and cyber attacks.

Creating stealthy communication networks
Stealthy communication networks are designed to be discreet and difficult to detect. By using hidden communication channels and encryption techniques, you can create a secure and stealthy network that is resistant to monitoring and eavesdropping. This allows you to communicate securely without the risk of interception.
Using hidden communication channels
Hidden communication channels are used to transmit data in a way that is not immediately apparent to outside observers. By concealing the communication within innocuous-looking traffic, you can avoid detection and keep your information secure. These hidden channels can be used to send encrypted messages that are difficult to intercept, providing an extra layer of security for your communication network.
Encrypting communications in stealthy networks
In stealthy communication networks, encryption is used to protect data as it is transmitted over the network. By encrypting communications, you can ensure that your information remains confidential and secure, even if it is intercepted. This prevents unauthorized access and helps to maintain the stealth of the communication network.
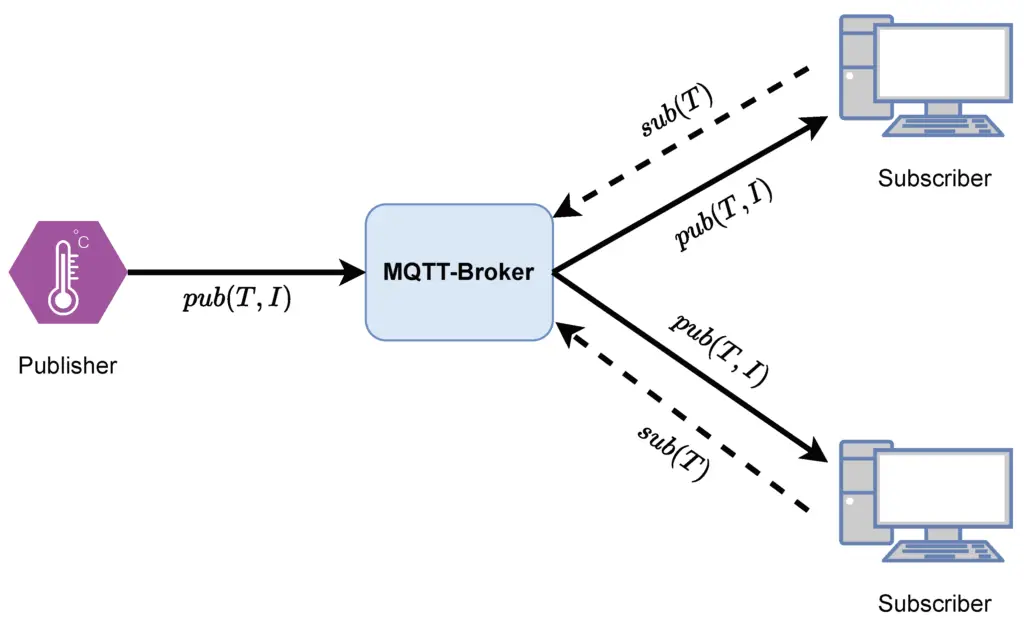
Tools for establishing secure and stealthy communication networks
There are several tools available that can help you create secure and stealthy communication networks. These tools provide encryption and hidden communication channels to protect your data and ensure the confidentiality of your communications. By using these tools, you can establish a secure and stealthy network that is resistant to monitoring and eavesdropping.
Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are a popular tool for establishing secure communication networks. By using encryption protocols to create a secure tunnel for data transmission, VPNs can protect your information from interception and unauthorized access. VPNs are commonly used to secure remote access to corporate networks and protect sensitive data from cyber attacks.
Secure messaging apps
Secure messaging apps are another tool for establishing secure communication networks. These apps use end-to-end encryption to protect messages as they are transmitted between devices. By using secure messaging apps, you can communicate securely without the risk of interception or eavesdropping. Secure messaging apps are ideal for transmitting sensitive information and ensuring the confidentiality of your communications.
Stealthy communication tools
Stealthy communication tools are designed to create hidden communication channels that are difficult to detect. These tools use encryption and obfuscation techniques to conceal data within innocuous-looking traffic, making it resistant to monitoring and eavesdropping. By using stealthy communication tools, you can establish a secure and stealthy network that is invisible to outside observers.
Conclusion
Establishing secure and stealthy communication networks is essential for protecting sensitive information and ensuring that your data remains confidential. By using encryption protocols, hidden communication channels, and secure messaging apps, you can create a network that is resistant to interception and eavesdropping. By following the steps outlined in this article, you can establish a secure and stealthy communication network to safeguard your information.